Sophisticated Invalid Traffic is an issue — a real, painful, and budget-wasting one.
You can’t protect yourself if you don’t understand where the threats are coming from, though – it’s like boxing with a blindfold on.
You know your Google Ads spend is getting wasted – the evidence is right there in front of you. Those clickers aren’t converting, and you’re pretty sure a lot of them have zero interest in buying.
So how do you stop it from happening? Well, you can’t fix what you don’t understand – and right now, you need to understand invalid traffic, so you can protect your ad budget, mitigate click fraud, improve your ROI and get better data.
We’re going to get right to it, so you can identify all the different kinds of invalid traffic and separate your friend from your foe from your… ‘who knows?’
Then we’ll go one better, giving you some solid strategies to help you detect unwanted invalid traffic – and keep it out of your campaigns.
What Is Invalid Traffic?
The most generally accepted invalid traffic definition is from Google (of course). Google defines invalid traffic as ‘any activity that doesn’t come from a real user with genuine interest.’
As you can see, this covers a lot of activity. And it’s not just bots, it’s people too. The Google definition continues:
‘It can include accidental clicks caused by intrusive ad implementations, fraudulent clicking by competing advertisers, advertising botnets, and more.’
The keyword there (assuming you already know about click fraud) is ‘accidental’.
Not all invalid traffic is specifically targeting your Google Ads spend – some of those visitors may just be confused humans. But if your Google Ads campaigns are properly targeted and implemented, and these confused users are still showing up in droves, it’s likely that someone is sending them there on purpose. And those clicks are still costing you money.
It’s also important to understand invalid traffic isn’t just an issue for your ads (although that’s where it causes the most damage). Invalid traffic causes problems for websites too, distorting your analytics and slowing your site. That’s why learning to identify and mitigate invalid traffic is an essential skill for anyone who relies on digital marketing.
Let’s start breaking it down – first of all, there are two main categories of invalid traffic, which are general invalid traffic (GIVT) and sophisticated invalid traffic (SIVT). Let’s get the GIVT out of the way first.
What Is General Invalid Traffic
GIVT is very much the lesser of two evils. Even though it’s not a ‘real user’, and there’s no ‘genuine interest’, a GIVT source has no intentions or potential to damage or disrupt your marketing activity. These sources are easy to identify and filter out of your campaigns and metrics, and are usually one of the following;
- Known data center traffic. If you’ve ever looked at Google Analytics and wondered why the good people of Ashburn, Virginia are so interested in your business, well, now you know.
- Spiders and search engine crawlers. Mapping out the internet so users can find you, these spiders (like their non-digital counterparts) are really useful creatures and you definitely shouldn’t squash them.
- Browsers that pre-fetch or pre-render data. Some modern browsers will pre-render data to provide a smoother, more seamless browsing experience, accessing pages to prepare just in case their human user chooses to visit.

Sophisticated Invalid Traffic, Explained
Here’s where your problems start – because Sophisticated Invalid Traffic (SIVT) sources don’t want to be found. Their whole purpose is to sneakily extract as much money as possible, without being blocked, so a lot of SIVT sources use strategies and techniques to evade detection. That’s what makes them sophisticated.
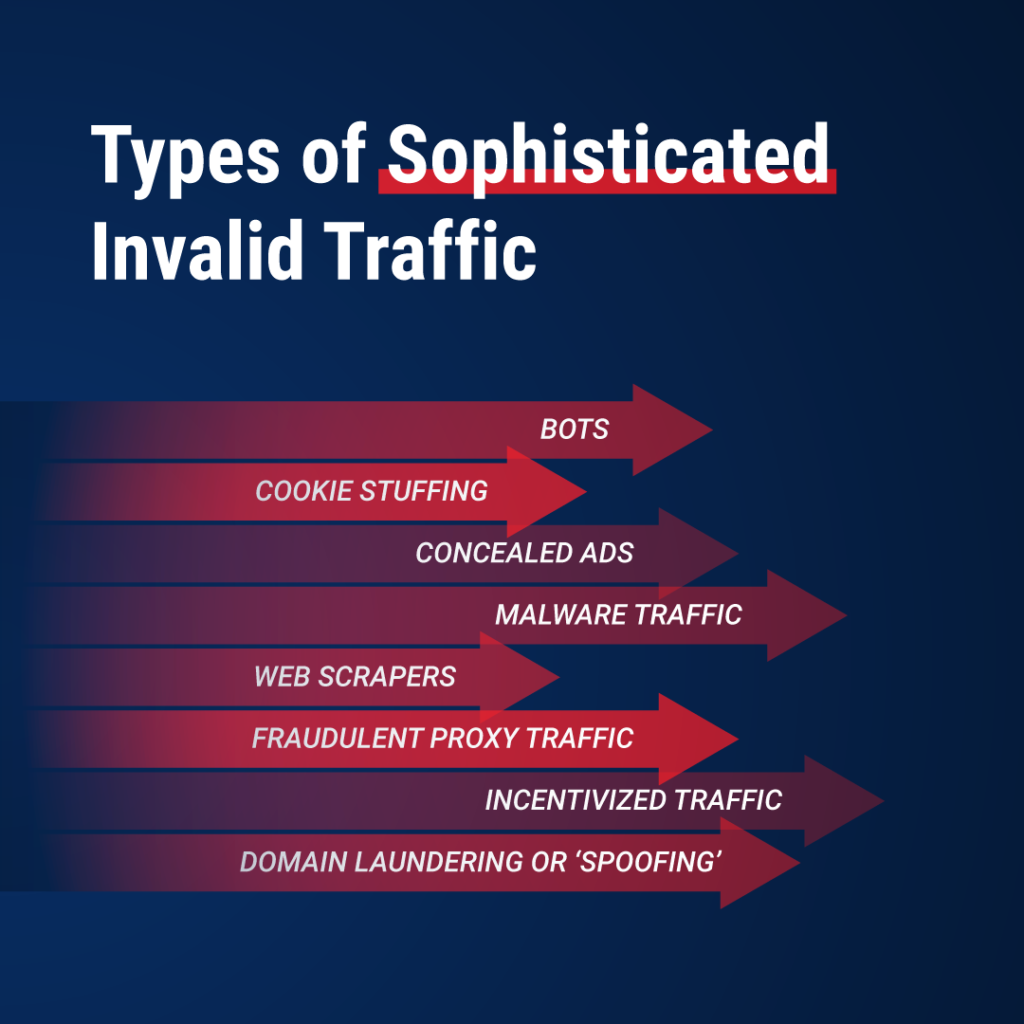
The Main Types of Sophisticated Invalid Traffic
It’s important to remember that not all of these Sophisticated Invalid Traffic sources are specifically targeting your Google Ads budget – some of these tactics are intended to steal from publishers or affiliate marketers. However, even if you’re not the target, it’s important to understand the techniques being used – it might be your advertising partners who are affected, and you don’t want that, either.
Bots
Repeatedly clicking ads is hard work. Nowadays it’s usually automated (although human click farms are still operational in parts of the world where labor costs are low).
Bots allow fraudsters to carry out click fraud at a massive scale, and while the speed and frequency with which bots operate is often a giveaway, many bots are now capable of mimicking human behavior, making them even harder to spot.
Cookie Stuffing
An issue that affects publishers and affiliate marketers, cookie stuffers will secretly insert large numbers of cookies into users’ browsers. These cookies will allow the cookie stuffer to take credit when that user eventually visits one of the sites associated with the fraudulent cookies.
The destination site then pays out to the cookie stuffer, not the publisher or affiliate that’s actually led the user there. The placement of the fraudulent cookie and the theft of the attribution fee can be separated by a period of time, which makes it even harder to identify the criminal.
Concealed Ads
Manipulating ad placement by stacking or hiding ads on the page, so they can be accidentally clicked by users who don’t know they’re there. This is a tactic used either by unscrupulous third-party promoters or the publishers themselves.
Malware Traffic
Malware is malicious software that infects a user’s device. The user’s device can then be controlled by the malware owner, and secretly used for click fraud (or other illegal activity), without the device user suspecting anything. Malware is distributed via adware – online content that will secretly install malware when you click on it.
Web Scrapers
These automated programs are used to gather specific data on a given subject. If someone is using a web scraper to gather data specific to your industry – pricing information, for example – then a web scraper may well connect to your website via your Google Ads campaigns, creating invalid traffic.
Fraudulent Proxy Traffic
Fraudsters may use a proxy server or a virtual private network (VPN) to conceal their IP address and location, making their click fraud harder to identify.
Incentivized Traffic
A third-party promoter or advertising partner may be using incentives without your knowledge to artificially inflate your traffic. It looks like they’re providing you with a good result, but all the extra traffic is only valid if it comes from sources with a ‘genuine interest’. If the third party is offering them product discounts or some other kind of reward, then that traffic isn’t likely to convert.
Domain Laundering or ‘Spoofing’
Another Sophisticated Invalid Traffic source generated by fraudulent publishing practice – a low-value publishing domain is disguised as another, more valuable domain, in order to charge a higher CPM (cost per impression). The ad is then rendered on the low-value site, where traffic may be manipulated further by bots or concealed ads.
App-based ads are also particularly vulnerable to this source of SIVT, in which case it’s known as app spoofing.
So as you can see, Sophisticated Invalid Traffic is a messy business. Almost every stage of Google’s advertising operations has been exploited for its weaknesses by unscrupulous parties. And none of it is good news for your Google Ads.
How To Detect Sophisticated Invalid Traffic
Understanding the causes and categories of invalid traffic gets us halfway there. Now we need to master the art of sophisticated invalid traffic detection.
Get a Feel for Your Site Traffic, So You Can Spot Irregularities
If you’re serious about stopping invalid traffic (like we are), you need to have a basic awareness of what your traffic looks like on most weeks. Check your traffic every week, and Sophisticated Invalid Traffic will stick out like the proverbial sore thumb.
For starters, look for single IP addresses with a lot of clicks on the same ad. Any that you find should be double-checked against your server logs. Root them out, then add them to your blocklists, and your advertising partner’s blocklists too.
Packet Headers Are a Dead Giveaway
If you aren’t afraid of getting technical (or if you’ve got a network administrator handy) you can inspect the packet headers of data packets associated with suspicious IP addresses.
Packet headers are a great source of information about your visitors, and very few fraudsters go to the effort of covering their tracks at this level. You can spot giveaways like;
- Many different device details on packets from the same IP. This usually indicates a proxy server.
- Hacker-friendly operating systems, like Linux. Open-source OS is the way to go, if cybercrime’s your thing.
- Outdated browser versions. Once the security updates stop, old versions of your favorite browsers become unstable, providing opportunities for fraudsters to exploit.
- Mobile devices with browser extensions. This usually indicates an attempt to disguise the device.
It’s worth keeping in mind that you’re looking for evidence of activities that have been purposely concealed, by people who spend most of their time figuring out ways to steal from you undetected. It’s not going to be easy. If you’re determined to investigate, here are some other big red flags you should know about if you’re manually searching out invalid traffic.
So…if you’ve spotted it, how do you stop it?
How To Stop (or at Least Mitigate) Sophisticated Invalid Traffic
Here are two of the main things you can do today to protect against SIVT (and some ‘how to’ tips if you need a little guidance).
Target Carefully
You can dodge a significant amount of Sophisticated Invalid Traffic, just by avoiding being in the wrong place at the wrong time. You’re already aware of the benefits of being specific with your Google ads targeting – but giving some thought to those you definitely don’t want seeing your ads can be useful.
Make sure you exclude geographic zones outside your target market, and any locations or geographic regions strongly associated with click fraud. Target your ads according to time zone, as well. If you’re only targeting customers within your own time zone, then pausing your ads during the night means you’re less likely to pick up unwanted clicks from other time zones..
Set Up and Use Your IP Exclusion Lists
A healthy, regularly updated IP exclusion list is an essential weapon in your fight against Sophisticated Invalid Traffic. Unfortunately, Google limits you to 500 exclusions. This sounds like a lot, until you consider the massive scale of many click fraud operations and the speed with which proxy servers can switch between IP addresses.
Active manual IP address exclusion management is the only way to stay on top of this – but it can quickly become a full-time job, particularly in more competitive industries where SIVT and click fraud have a major impact on Google Ads campaigns.
A dedicated click fraud prevention solution is the most cost and time-efficient way to manage your exclusions. Our dedicated team will automate and optimize your IP exclusion list regularly.
ClickGUARD Breaks Down the Sources of Your Invalid Traffic, and Optimizes Your Ad Campaigns
Now you understand the many sources of invalid traffic, and the work involved in successfully protecting your budget from SIVT…maybe you want an easier solution?
ClickGUARD tracks and stops SIVT, click fraud, bots, and wasteful traffic, so you can make the most out of your Google Ads efforts.